1 in 2 organizations were impacted by a social engineering attack in 2022.1
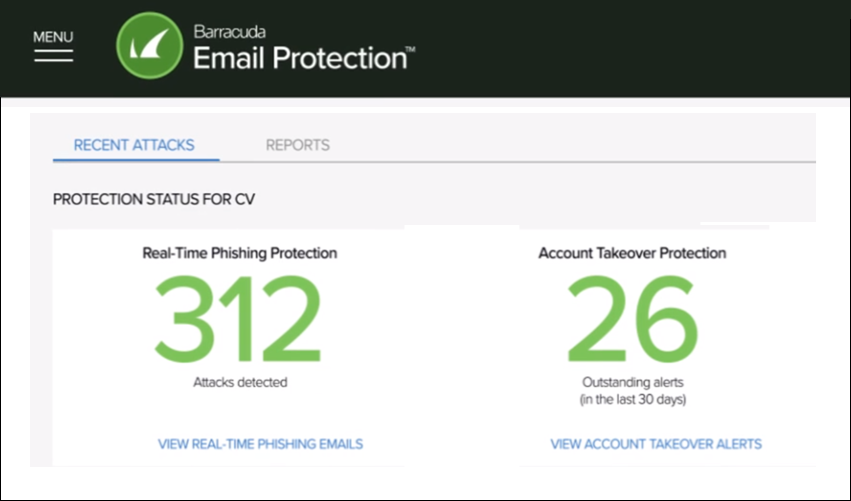
Get protected with Barracuda's AI.

34%
more phishing blocked than Microsoft.

99.2%
of phishing attacks blocked without manual configuration.

20,000+
organizations trust Barracuda's AI globally.
Stop phishing attacks.
Barracuda provides easy API integration with Microsoft 365 for ultimate protection against personalized threats. With its unmatched ability to analyze patterns, detect anomalies, and recognize evolving tactics, Barracuda's AI stays one step ahead of cybercriminals.
Unlock superior detection accuracy.
Barracuda AI-powered email security excels at identifying targeted threats with high accuracy, reducing the risk of successful attacks. Our AI continuously fine-tunes your email security by learning from patterns and behaviors, reducing false positive rates.

Secure email in real time.
Barracuda's AI analyzes emails in real time and takes immediate action to prevent malicious messages from reaching users. Upon detection, malicious emails are immediately purged from inboxes, eliminating the risk of user interaction.

Save IT resources without compromising efficacy.
AI-powered security allows for robust threat prevention without customer configuration. With high detection efficacy, there's no need to instruct the system on threat detection methods or create error-prone detection policies.

Assess your security posture with Email Threat Scanner.

Join 16,000 organizations who have already used our free Barracuda Email Threat Scan to identify personalized email attacks currently sitting in their users’ inboxes.
- Start your free scan in less than 5 minutes.
- Get results fast.
- No impact on email performance.
Barracuda's award-winning technology
See why across the globe Barracuda Impersonation Protection wins praise for its cutting-edge technology and innovation.

Phishing and Impersonation Protection are included in Barracuda Email Protection.
Discover the right plan for you.
